Some of the largest frauds in history occurred because an agent contracted to act on someone’s behalf, decided to act in their own self-interest instead. This talk given to economists at APEE explains how basic cryptography could have prevented some of those major frauds and changed the nature of the principal-agent problem.
Slides
Download all slides as a pdf here.
Recording
The talk was re-recorded on Youtube here.
Transcript
Hi, my name is Kate Sills. I’m a software engineer, and I was the lead engineer for the Agoric blockchain’s smart contract framework. Today, I’m going to be talking about reducing agency costs using digital signatures. This was originally a talk I gave at APEE 2022 for an audience of economists.
Let’s start with some groundwork in economics: In 1979, in their paper Theory of the Firm, Jensen and Meckling defined the agency relationship as a contract in which one person (the principal) engages another person (the agent) to perform some service on their behalf and delegates some decision-making authority to the agent. Importantly, the interests of the principal and the agent may diverge, which we call the principal-agent problem. The agent may do things that harm the principal. As an example, if I take my car into the Mazda dealership to be serviced (to choose an example completely at random,) I’m the principal, they’re the agent, and they might try to sell me things I don’t need. They would benefit, but I would not, and I’m reliant on them for information about my car. We call these kinds of costs that arise due to the divergence of interests agency costs.
Agency costs can be split into three parts:
The monitoring expenditures by the principal. (For instance, if I take the day off work to double-check my mechanic’s actions.)
+ the bonding expenditures by the agent (For instance, the mechanic might commit to a money-back guarantee.)
+ the residual loss (This is the monetary loss due to the divergence of interests—for instance, the cost of unnecessary spark plugs.)
Today I’m mostly going to be addressing the monitoring costs expended by the principal.
Additionally, Oliver Williamson provides another way to look at this. He’s concerned with opportunism (which he defines as self-interest-seeking with guile). But, he says, you can reduce this opportunism by supplying cost-effective safeguards. So for instance, I might look at the Yelp reviews for car mechanics and thus avoid contracting with shady mechanics.
Williamson points out that studying the prevention of opportunism requires more knowledge of the specific contractual devices and safeguards than is usual in economics. So we’re going to go into the weeds a bit here on a very particular instance of opportunism and a particular safeguard, but I’m pointing out ahead of time that Williamson says it’s ok!
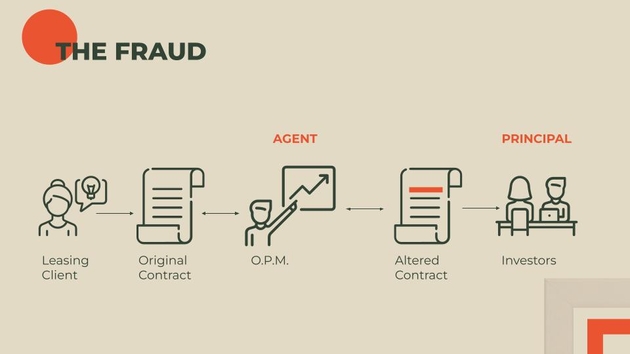
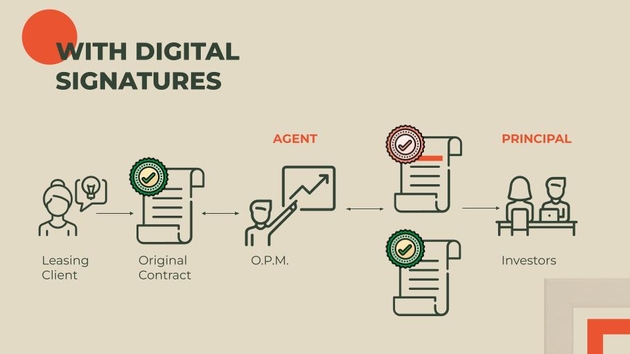
Let’s talk about an example of opportunism! OPM Leasing Services was a computer leasing company in the 1970s that committed fraud in excess of 200 million dollars. The way their business was supposed to work was this: They would buy mainframes and lease them out to companies. They would then take those leasing contracts and sell them to investors like Goldman Sachs and Lehman Brothers, taking care of all the residual value.
OPM had total control of information, so the principal, let’s say, Lehman Brothers, was entirely reliant on OPM, the agent, to be behaving honestly.
They were definitely not behaving honestly.
One of the things they would do is alter the contracts that they had previously signed with clients. Here we have the leasing client, and OPM, and the original contract that was signed. They would bump up the value of the computer assets, before sending the altered contracts to the investors, the principal. According to the book Lying for Money, they would use the glass table in their reception area, and one of them would shine a flashlight underneath the table, and the other would trace the signature of a leasing client in order to forge the signature on the altered contract.
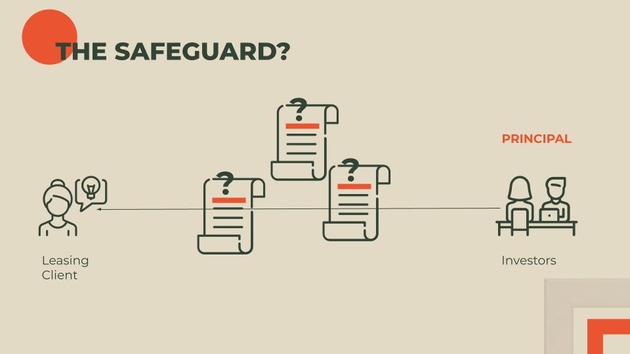
So, you might say, to prevent something like this, Lehman Brothers should have asked for direct contact with each of the leasing clients and asked them to each confirm the details of the contracts. That’s a significant amount of legwork, not just for one contract, but all of them. But there’s an easier way. And that easier way uses cryptography.
What is Cryptography? Cryptography is the study of secure communications. Only the sender and the recipient can read the message, even if the message falls into the wrong hands.
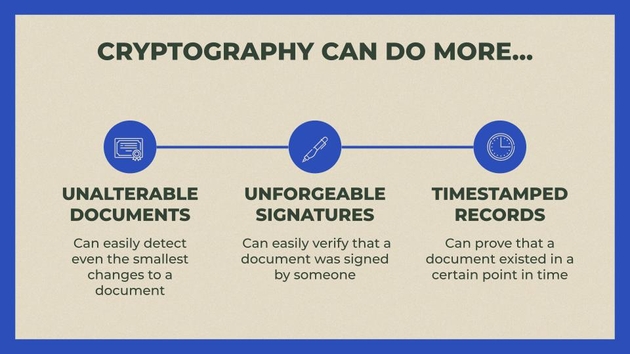
What does cryptography have to do with monitoring costs? Well, in addition to being able to encrypt and decrypt messages, cryptography allows us to do things like:
-
Guarantee that a document is unaltered,
-
Prove a document was signed by a particular party,
-
Prove a document existed at a certain point in time and wasn’t created later.
So in this case, it sounds like we want to verify that the document was actually signed by the leasing client, and was not altered after the signature. For that, we need digital signatures.
So by a digital signature, I don’t mean just electronic signatures.
I don’t mean this on the left. What I do mean is on the right. On the top right, is how Adobe represents a digital signature. But a digital signature is just data, so on the bottom right hand of this slide, the numbers and letters is a digital signature as well.
In a digital signature, you have two pieces of information. What is called your private key, which you keep private, and your public key, which you share widely. Only you, or the holder of the private key, can sign with your signature. But anyone with your public key can easily verify it!
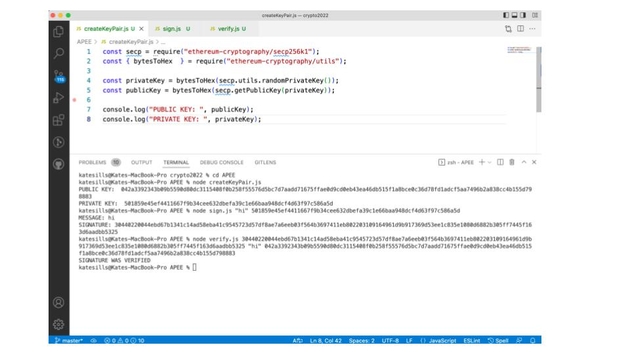
Here’s some example code creating a public and private key and then signing a message, then verifying that the message was actually signed by the entity holding the private key.
With digital signatures, there are two roles. The Signer publishes their public key and then digitally signs the document, and then a separate person, the Verifier, looks up the public key and then given the signed document, is able to verify the signature.
In the OPM case, if the leasing clients had 1) published their public key (perhaps on their website), and then 2) digitally signed the contracts with their private key, then the investors, when given a contract supposedly signed by the leasing client, would have been able to look up the public key, and verify the signature. The leasing client only has to post one piece of data: their public key. And the signature and the document can both be gotten safely from OPM, even though they’re completely untrustworthy.
This would only use cryptography—once the investor has the public key for the leasing client, it would not require any further interaction with the leasing client. It would not even require internet access. It takes less than a few seconds and the cost is basically nothing.
Digital signatures are in use now, for instance, I mentioned that Adobe has a digital signature tool. Here’s a picture of an Estonia ID card that has a chip that can do digital signatures and store a private key.
Also, credit cards use public-key cryptography and create digital signatures, and this is how they know the credit card was in use in a particular location.
This is a hardware wallet used in the cryptocurrency world to store the private key that is used to digitally sign cryptocurrency transactions. Holding the private key is seen as ownership of tokens.
But let’s talk about another fraud example. In California’s Central Valley, there have been millions of dollars of nuts stolen in the past 10 years. Why? Nuts out of the field are raw agricultural materials - you can’t put a barcode on it. And they’re expensive. A single truckload is half a million dollars. In this chain of thefts, a truck driver would show up, his paperwork would check out, and he would drive off, but the nuts would never reach their destination.
There were safeguards! The farm staff would photograph the truck, and even receive a thumb print from the driver.
What was happening is that the thieves would put together fake documents based on public information, then pay a truck driver in cash to perform the job, claiming that they were a legitimate business and just needed more help. So when the truck driver got caught, he knew nothing about where the nuts had gone beyond where he had dropped them off.
So we can imagine that the truck driver could use a smart card like the Estonian ID, and thus prove his identity in a way that isn’t forgeable like driver’s licenses or trucking paperwork is.
That leads to the question of why isn’t this in use already? Why is there money on the ground? I think there’s a number of reasons.
First, cryptography has historically been affected by legal battles. It was illegal to export cryptography methods from the US, because it was deemed an export of munitions. Then in the 90s, there were the Clipper Chip fights where the government tried to put backdoors into cryptography.
Second, there’s a disconnect between cryptographers who are mostly mathematicians, and the people who need the solutions, who are business people, including farmers and truck drivers.
Third, it’s difficult to create and teach new rules of interaction. For instance, in the case of the nut theft in California, we would have to teach the farmer how to receive and store the public key from the trucking company. We’d have to teach the truck driver how to use the id card to sign bills of lading. We’d have to have procedures for what happens when the private key is accidentally shared and the key pair needs to be revoked.
Lastly, as a software engineer, I know it’s difficult to write good software. As an example, they found that the Estonian ID cards had been produced wrongly, such that some of the cards shared the same private key. This would mean that some people could create the signatures of other people, defeating the key property of digital signatures—only you, as the holder of the private key can create your signature. So it’s very hard to write good software, but I will point out, it’s never stopped us before.
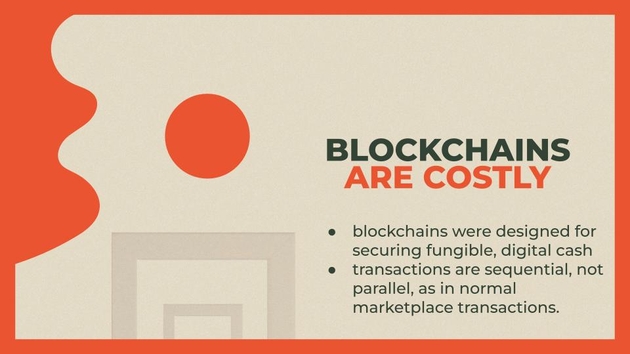
Lastly, I just want to compare the costs of digital signatures to blockchains. Like I said, signing and verifying a digital signature is very very cheap. Probably as cheap as typing a word into your word doc. Blockchains, by contrast, are very costly. The reason for that is because blockchains were designed to secure fungible, digital cash. If you have counterfeit money in the system, the value decreases for all money. So because of that, transactions are sequential and checked by the entire network, whereas in the normal marketplaces, only a few people care about every transaction so those can happen in parallel. So decentralized blockchains in the form of Bitcoin or Ethereum are inherently expensive.
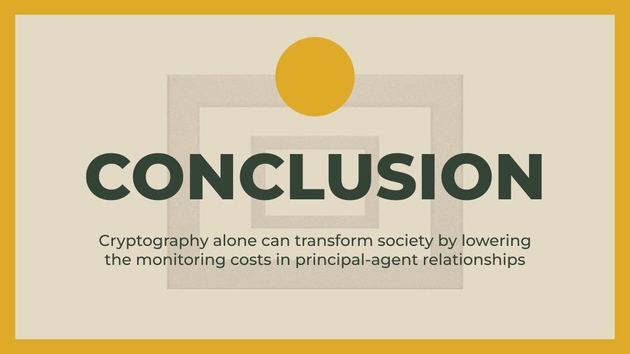
In conclusion, there is a lot of excitement around blockchains transforming society. Blockchains use cryptography to make decentralized digital cash possible. But, a lot of the cryptography that blockchains use, has been around since the 1970s, and is useful in and of itself. That cryptography itself can transform society, in particular, significantly lowering the monitoring costs in principal-agent relationships.