I gave this lightning talk at the Foresight Crypto, Security, and AI Workshop in 2022 to a group that included software engineers and economists. I talk about how we have expensive auditing and financial control processes in business, and how we have cheap cryptographic tools that can solve some of these problems instead. Importantly, despite the hype, these tools aren’t blockchains themselves.
Recording
Slides
Download all slides as a pdf here.
Transcript
Hi, I’m Kate Sills. I’m a software engineer, and previously worked at Agoric with Mark Miller, where I built Zoe, Agoric’s smart contract framework.
We have these very costly problems in the real world: fraud and other kinds of malicious behavior, and we have costly solutions, such as controls and policies and procedures, and auditing to ensure that we follow these controls, and in some cases, such in the case of payment fraud, we’re using AI to try to detect it.
And then on the other side, we have these very powerful cryptographic tools: hashes, digital signatures, hash pointers. Given that I only have 7 minutes, I’m not going to go into detail about what all of those are, but the point is, we have all of these tools and yet the general public knows nothing about them. Something is missing.
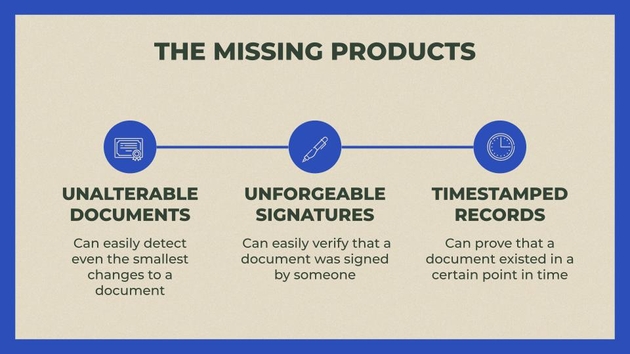
Just to go into detail into what these products might look like: with hashes, we can create unalterable documents where if there’s even the slightest change, the hashes won’t match and we can tell that something has changed.
With digital signatures, we can create unforgeable signatures. Unlike a regular or electronic signature where anyone can create it, with a digital signature if you have the private and someone else does not, they cannot forge your signature.
With hash pointers, effectively blockchains, we can create timestamped records and prove that a document existed at a certain point in time and was not just created after the fact and inserted in place.
So then there’s the question: why aren’t we using the cryptographic tools?
In many cases, we are, and the general public doesn’t realize it. For instance, a credit card with a chip can have a private key on it that creates digital signatures. For software verification, all sorts of things. But the general public has no idea.
Second, I think there’s a disconnect between the cryptographers who are mostly mathematicians and the people who actually need their problems to be solved, who are mostly business people. These two groups are just not talking.
Third (and I’m very sorry to all the cryptographers in the room) but cryptographers are not known for good user experience design. There’s this famous paper called Why Johnny Can’t Encrypt that’s from 1999 and it goes through user studies. I think they had maybe 20 users or so trying to use PGP and they were not able to do basic tests, so something is broken there.
And then fourthly, I think there’s confusion about blockchains. All the things I mentioned such as making sure documents haven’t been altered, I think the general public hears about this and they attribute them to blockchains and cryptocurrencies and think that you need blockchains. But in reality, Bitcoin, while it was incredibly innovative in solving the double spending problem and figuring out how to do that without using the central authority, Bitcoin didn’t invent hashes, it didn’t invent digital signatures. We’ve had digital signatures since the 70s. And Bitcoin did not invent blockchains so to speak. The word “blockchain” came after Bitcoin, but if you look at bitcoin’s references in the Bitcoin whitepaper, one of those references is a 1991 paper by Haber and Stornetta that’s about timestamping services and using hash pointers as part of these timestamping services to make sure the documents aren’t created currently and inserted back in time.
So I know I don’t have much time here, but I want to go over what a timestamping service actually looks like according to the Haber and Stornetta paper.
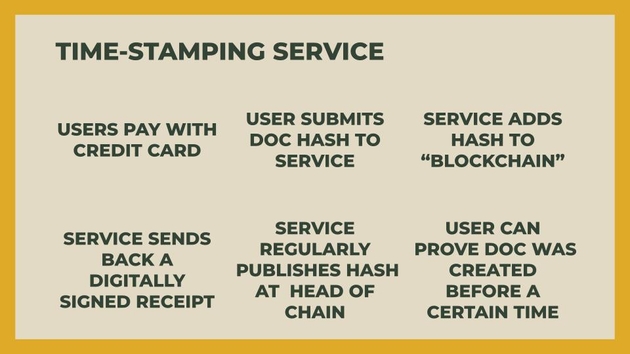
So you can imagine that users pay with a credit card (there’s no cryptocurrency involved).
The user submits a document hash to this service.
The service adds the hash to a chain of hash pointers (a blockchain) but they’re the only one’s adding it so it’s centralized, in that there aren’t multiple parties adding transactions. It’s only them.
And then the service sends back a digitally signed receipt so that the user can have this proof that at least the service says that this is in the blokchain, and then the service regularly publishes the hash at the end of the chain to somewhere they don’t control, like say, in a newspaper or another blockchain, perhaps a decentralized one.
And then finally the user can prove that the document was created before a certain point in time.
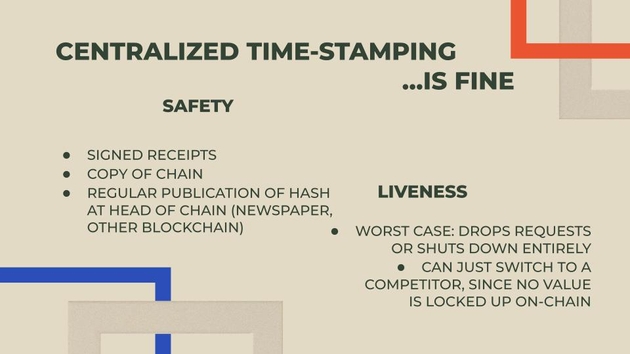
So I want to say something kind of controversial here. What I’m going to argue is that for the timestamping service centralization is actually fine. So I’m going to divide it up into two parts which is safety and liveness.
For safety, we have the cryptography. We have the signed receipts, we have the user who can have a copy of the chain, and if there’s regular publication of the hash at the tail of the chain in the newspaper or other blockchain, we know that nothing has been altered in that chain. So for safety, we’re fine as long as we have the cryptography.
Then for liveness, the worst case scenario is very different than in a cryptocurrency scenario. So for your timestamping documents the worst case scenario is that your centralized service drops requests just kind of willy-nilly or it shuts down entirely. Since it’s just a timestamping service you could switch to a competitor. Unlike a cryptocurrency there’s no value locked up on chain. As long as you keep a copy of the chain, you can prove that you document existed at a certain point in time even if that service goes down. That’s my controversial statement; hopefully we can talk about it later.
My takeaway is that decentralized blockchains are costly. You have this global consensus about the ordering of transactions and we have all of these problems in business where we have very costly solutions like controls and auditing. But cryptographic tools are incredibly cheap - as cheap as typing a letter into your word doc - and I think we should be using those. I’m interested in creating the products that bridge this gap.
Thank you, and I have time for a few questions.